This is the first part of the two part series on security by isolation. In today’s environment everyone is concerned with security. I am not any different. I practice standard safe practices by using a lower privileged user account, keeping the anti-virus updated, regularly applying security patches to the operating system and web browsers. I scrutinize emails I receive and do not open any suspicious attachments. Those are all good practices that make me feel safe and protected. Unfortunately they are not very effective.
Even though I had been aware of these facts I did not know how to address them. Reading the interview with Joanna Rutkowska on Tom’s Hardware and her blog post ‘The three approaches to computer security‘ inspired me to implement my own security by isolation. If you have time to spare I suggested you read the articles. Otherwise I am going to try to summarize them briefly.
Most major operating systems implement several approaches to security by isolation. Process address space separation, access control lists (ACLs), and Sessions are some of more common ones used in contemporary operating systems. Despite these architectural designs OSs allow third-party drivers to operate at the same privilege level as the rest of the kernel. A bug in a driver can allow an attacker to compromise the system by bypassing protection mechanisms provided by the OS.
Home implementation
Inspired by Joanna’s setup I decided to implement security by isolation on my home computer. The implementation consists of three virtual machine guests running on top of Vista 64-bit host. I have tried different virtualization products, Virtual PC, VMware server, and VirtualBox just to name a few. They are all free virtualization products. I found VirtualBox to be the best suited for my needs because of multiple snapshot capability and open source license. It supports Windows and Linux guest operating systems which was a relevant factor to my final choice.
As I have already mentioned before there are three VMs each one providing a different level of security suited to its role. The ‘Red’ VM is the least secure one and it is meant to be used for everyday browsing. The ‘Yellow’ VM is more secure than the Red one. It is used for online shopping exclusively. The most secure of all of the VMs is used for online banking only. Therefore it is appropriately named ‘Green’.
The ‘Green’ virtual machine
The sole purpose of the ‘Green’ VM is online banking with only two banks I have accounts with. It is not suppose to be used for anything else. No programs besides firewall GUI are installed on top of the default Ubuntu installation. It is characterized by the highest level of security. It satisfies following characteristics:
- Uses secure operating system.
- Only allows outbound internet traffic to two banking websites. Blocks all other traffic.
- Does not store any private data in the browser.
Here is how I was able to achieve the specified goals. I decided to install Ubuntu because of reduced potential of a system compromise in comparison to any other Windows version. After all, there are not that many evil people targeting Linux.
Firewall setup
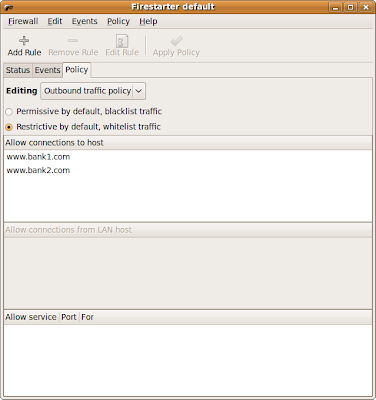
I installed Firestarter firewall which is a GUI for Ubuntu’s out of box firewall. The firewall blocks all incoming traffic by default:
I white-listed outgoing traffic to the two banking websites I have an account with:
I made few tweaks to the firewall ICMP filtering settings:
Firefox setup
Ubuntu comes with preinstalled Firefox which is my favorite browser. Since Firefox does not support an “Incognito” mode as Chrome or IE8 do, I had to make some changes to it. First I disabled all history features under privacy setting:
The last Firefox setting I modified was concerned with caching under ‘about:config’:
Conclusion
The whole ‘Red’ system setup took less than a day. It is a pretty good time investment considering the benefits. I have been very pleased with it so far. The only thing I wish was different is availability of an “Incognito” browsing mode. Hopefully the next version of Firefox will have it. Otherwise I will have to wait until Chrome for Linux is officially released.
In the next week’s post, ‘Security by isolation – The ‘Yellow’ and ‘Red’ machines’ I will describe the ‘Yellow’ and the ‘Green’ system setups. Until then please share your opinions, suggestions, and questions in the comments section.







Very interesting, though I may be too lazy to do the same thing 🙂 If you get a chance, you should do a write up on VirtualBox. I've never used it before, but I'm intrigued that you like it better than the other ones out there.
@James – It is not that much work. You can download free Ubuntu virtual appliance with Firefox installed. You only need to install the firewall and configure Firefox and firewall.
I was thinking about writing about VirtualBox, but know that you mentioned it I will put it on the “topic list.”